The Conversation
-

Saying ‘I’m not good at maths’ is not cool – negative attitudes are affecting business
A new report by the Australian Industry group claims that low literacy and numeracy skills in the Australian workforce are affecting business.
-

Five key findings from 15 years of the International Space Station
Humans have now been living on the International Space Station for 15 years. Here’s what we’ve learned.
-

Fat-burning fat exists, but might not be the key to weight loss
The potential health benefits of energy-burning brown and beige fat might be not the effect on weight, but rather on blood sugar and cholesterol.
-
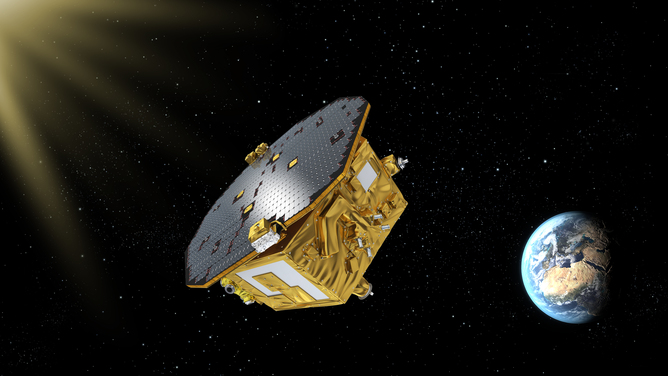
LISA Pathfinder will pave the way for us to ‘see’ black holes for the first time
It has been a century since Einstein presented his theory of general relativity but it is still helping us unveil some of the deepest mysteries of the universe. Now the […]
-

Why cats are fussy eaters but dogs will consume almost anything
Cats share some important genes associated with herbivores – this might explain their particular eating habits.
-

What’s it like to see auroras on other planets?
Witnessing an aurora first-hand is a truly awe-inspiring experience. The natural beauty of the northern or southern lights captures the public imagination unlike any other aspect of space weather. But […]
-
Do trees really help clear the air in our cities?
Some recent studies have suggested that trees may in fact worsen urban air quality by trapping pollutants at street level.
-

The chemistry that could feed life within Saturn’s moon Enceladus: study gives clue ahead of flyby
Saturn’s 502km-diameter icy moon Enceladus has fascinated scientists since it was first seen up close by NASA’s Voyager probes in the 1980s. The moon is venting plumes of ice particles […]
-

The future of scientific publishing: let’s make sure it’s fair as well as transparent
Scientific publishing has undergone a revolution in recent years – largely due to the internet. And it shows no sign of letting up as a growing number of countries attempt […]